In Ssl Tls Does Client Generate The Session Key
The Transport Layer Security (TLS) Handshake Protocol is responsible for the authentication and key exchange necessary to establish or resume secure sessions. When establishing a secure session, the Handshake Protocol manages the following:
- Cipher suite negotiation
- Authentication of the server and optionally, the client
- Session key information exchange.
Both client and server establish a session key. The server (or the client and server) then authenticate by performing signature-generation (for authentication). This has the advantage that each session needs to be attacked separately. This is known as (perfect) forward secrecy. DHE and ECDHE ciphersuites work differently. The key pairs are generated on the fly; i.e. The key pairs are ephemeral (the E in DHE). Both client and server establish a session key. The server (or the client and server) then authenticate by performing signature-generation (for authentication). This has the advantage that each session needs to.
Cipher Suite Negotiation
- Secure symmetric encryption achieved: The handshake is completed, and communication continues using the session keys. All TLS handshakes make use of asymmetric encryption (the public and private key), but not all will use the private key in the process of generating session keys.
- Mar 31, 2019 TLS Security 5: Establishing a TLS Connection. The process of establishing a secure SSL/TLS connection involves several steps. SSL/TLS security protocols use a combination of asymmetric and symmetric encryption. The client and the server must negotiate the algorithms used and exchange key information.
- Sep 13, 2012 By the end of the video, Keith will show you a high level overview on how SSL can effectively set up shared keying materials on both sides, instantaneously.
- This article explains how to generate certificates, set up key rings, and connect the certificates to the key rings. This article includes a scenario to set up certificates and key rings for a basic client/server FTP handshake, using Transport Layer Security (TLS).
- Jan 08, 2020 SSH (Secure Shell) and SSL/TLS (Secure Sockets Layer/ Transport Layer Security) are very similar as compare of security aspects – encryption, authentication and integrity processes. But when you are hunting for SSH vs SSL/TLS, here we are exploring similarities and differences between SSH vs SSL/TLS protocols.
The client and server make contact and choose the cipher suite that will be used throughout their message exchange.
Authentication
In Ssl Tls Does Client Generate The Session Key Error
In TLS, a server proves its identity to the client. The client might also need to prove its identity to the server. PKI, the use of public/private key pairs, is the basis of this authentication. The exact method used for authentication is determined by the cipher suite negotiated.
Key Exchange
The client and server exchange random numbers and a special number called the Pre-Master Secret. These numbers are combined with additional data permitting client and server to create their shared secret, called the Master Secret. The Master Secret is used by client and server to generate the write MAC secret, which is the session key used for hashing, and the write key, which is the session key used for encryption.
Establishing a Secure Session by Using TLS
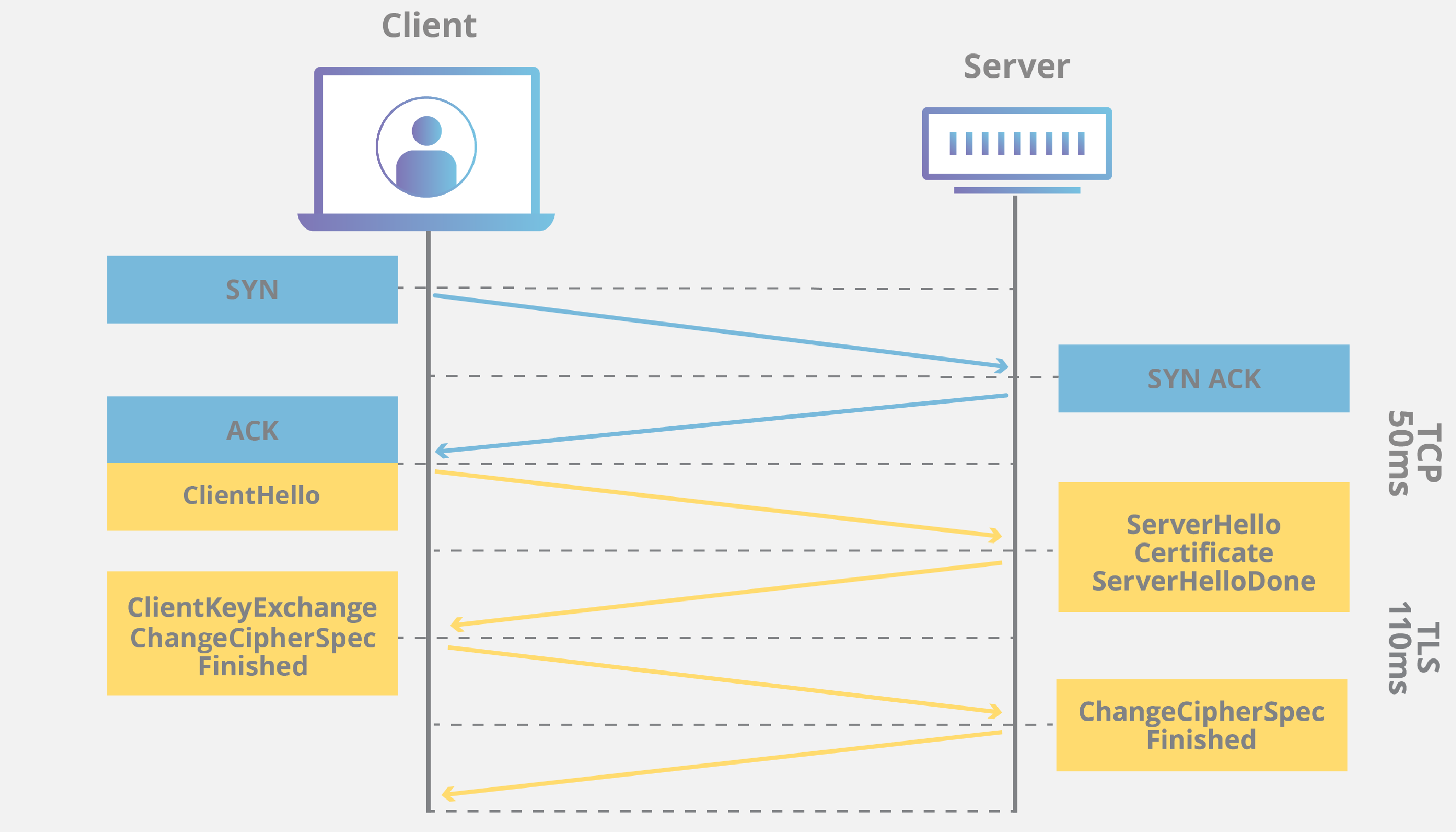
The TLS Handshake Protocol involves the following steps:
In Ssl Tls Does Client Generate The Session Key In Word
- The client sends a 'Client hello' message to the server, along with the client's random value and supported cipher suites.
- The server responds by sending a 'Server hello' message to the client, along with the server's random value.
- The server sends its certificate to the client for authentication and may request a certificate from the client. The server sends the 'Server hello done' message.
- If the server has requested a certificate from the client, the client sends it.
- The client creates a random Pre-Master Secret and encrypts it with the public key from the server's certificate, sending the encrypted Pre-Master Secret to the server.
- The server receives the Pre-Master Secret. The server and client each generate the Master Secret and session keys based on the Pre-Master Secret.
- The client sends 'Change cipher spec' notification to server to indicate that the client will start using the new session keys for hashing and encrypting messages. Client also sends 'Client finished' message.
- Server receives 'Change cipher spec' and switches its record layer security state to symmetric encryption using the session keys. Server sends 'Server finished' message to the client.
- Client and server can now exchange application data over the secured channel they have established. All messages sent from client to server and from server to client are encrypted using session key.
In Ssl Tls Does Client Generate The Session Key In Firefox
Resuming a Secure Session by Using TLS
The client sends a 'Client hello' message using the Session ID of the session to be resumed.
The server checks its session cache for a matching Session ID. If a match is found, and the server is able to resume the session, it sends a 'Server hello' message with the Session ID.
Note
If a session ID match is not found, the server generates a new session ID and the TLS client and server perform a full handshake.
https://amazingtree354.weebly.com/blog/download-google-dropbox-for-mac. Client and server must exchange 'Change cipher spec' messages and send 'Client finished' and 'Server finished' messages.
Client and server can now resume application data exchange over the secure channel.